WhatsApp 2FA: Secure Yourself From This Simple Hack
Imagine someone has taken over your account, what would happen to you and the people who contact you on WhatsApp?
Just as it is easy to fresh install of WhatsApp for your new phone is also how easy an attacker would gain access to your WhatsApp and possibly start a conversation with your friends claiming it is you.
Most times, the direct risk is not to you if you’re attacked, but to your contacts. They can expect to receive requests for data or even emergency funds. This is social engineering at its best. We would trust an end-to-end encrypted platform, a message from a trusted friend and so are coded to have our guards down and rather feel pity in these circumstances.

The repercussions of this happening are beyond imagination. This can even further spread to more of your contacts having there WhatsApp accounts taken over.
With the account taken over, the attackers could then message contacts in the groups you are in as if from the account holder (you), as well as any other contacts whose WhatsApp messages were received after the take over. No legacy data is compromised. The target device remains untouched. WhatsApp has simply been ghosted onto an illegitimate device.
It is surprising how many people have not yet enabled the Two-step verification PIN in WhatsApp—almost everyone we have asked has yet to set it up. If you’re the same, then please take that minute and set it up now.
The Question now is, How do we prevent this from happening to you for the first time or again?
WhatsApp introduced a feature where you can set a PIN of your own choice and even an email address just in case you forget your PIN. The PIN is your own verification to confirm that it is you even after inputting the SMS verification so you do not otherwise have to share your PIN with anyone.
You can find this feature in your WhatsApp setting > Account > Two-step verification: There you will be prompted to enable your PIN and confirm it, then you will also be asked to type in an email address to use to recover your account in case you forget your PIN
What you need to know about Delayed Phishing/ Post-Delivery Weaponized URL
Truth is, most of us have ever been a victim of phishing before and with the abundant resources online and trainings that we have so far had, we have become sort of immune to phishing.
Click here to as well look at our blog post about phishing and what you need to know
Our immunity against phishing has so far been boosted by e-mail service providers, mail gateways and even browsers that we use which has all embedded in their systems anti-phishing filters and malicious address scanners.
With all these above, cybercriminals are constantly inventing new, and refining old, circumvention methods. One such method is delayed phishing.
Delayed phishing is an attempt to lure a victim to a malicious or fake site using a technique known as Post-Delivery Weaponized URL.
“As the name suggests, the technique essentially replaces online content with a malicious version after the delivery of an e-mail linking to it. In other words, the potential victim receives an e-mail with a link that points either nowhere or to a legitimate resource that may already be compromised but that at that point has no malicious content. As a result, the message sails through any filters. The protection algorithms find the URL in the text, scan the linked site, see nothing dangerous there, and allow the message through.”
Effecting the malicious link
Attackers operate on the assumption that their victim is a normal worker who sleeps at night. Therefore, delayed phishing messages are sent after midnight (in the victim’s time zone), and become malicious a few hours later, closer to dawn.
If cybercriminals find a specific person to attack, they can study their victim’s daily routine and activate the malicious link depending on when that person checks mail.
Technology behind Delayed Phishing
For delayed phishing to be effective, hackers use at least one of these 2 common methods:
- Simple link: In this case, the hackers are the ones who are controlling the target site in that at the time of delivery, the site is safe so it can go through the several security levels it is scanned before it is delivered to your mailbox. At the time of delivery, the link leads to either a meaningless stub or (more commonly) a page with an error 404 message and the malicious version of the site is activated after delivery.
- Short-link switcheroo: Several sites offer link shortening services to the world, with this you can get alternative links that are easy to remember and short instead of long and boring links. However, some of this services allow you to alternate the link behind these short links. So the cybercriminals take advantage of this in that, by the time they are sending the email, the short link it pointing to a legitimate site and is swapped to the malicious site after delivery.
Although there is a third technology that is not so common which includes a randomized and short link where there is a probabilistic redirection. That is, the link has a 50% chance of leading to google.com and a 50% chance of opening a phishing site. The possibility of landing on a legitimate site apparently can confuse crawlers (programs for automatic information collection).
– Spotting & fighting Delayed Phishing
Ideally, there is need to prevent the phishing link from getting to the user, so rescanning the inbox would seem to be the best strategy.
In some cases, that is doable: for example, if your organization uses a Microsoft Exchange mail server. Kaspersky Security for Microsoft Exchange Server is also included in our Kaspersky Security for Mail Servers and Kaspersky Total Security for Business solutions.
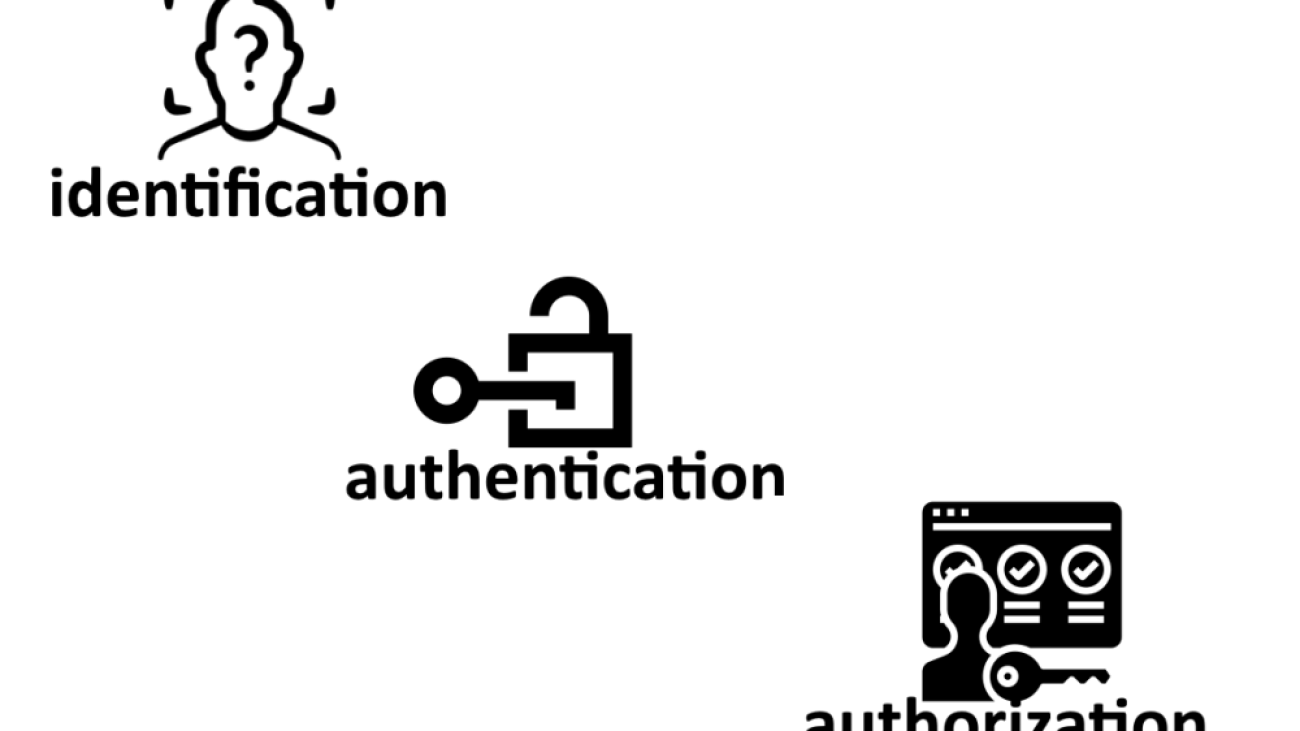
Difference between Identification, Authentication & Authorization
We all have been identified, authenticated and authorized almost everyday of our online life.
What we do not know most of the time is where each of this comes in while accessing our online platforms and we end up confusing the 3 words often using the terms identification or authorization when, in fact, they are talking about authentication.
But as long as we are able to understand what we are talking about, it has not mattered to us to get the meanings of these 3 words.
It is always better to know the meaning of the words you use, though, and sooner or later, you will run into a geek who will drive you crazy with clarifications, whether it’s authorization versus authentication, fewer or less, which or that, and so on & to be honest, you could even catch an attitude!
So what do these 3 words actually mean?
- Identification occurs when a subject claims an identity (such as with a username)
- Authentication occurs when a subject proves their identity such as with a password (for example, by comparing the password entered with the password stored in the database)
- Authorization techniques can grant or block access to objects based on their proven. This is the function of specifying access rights/privileges to resources.”
🙂
So, now you know in what ways identification is different from authentication and authorization. One more important point: Authentication is perhaps the key process in terms of the security of your account. If you are using a weak password for authentication, your account could easily be hijacked. Therefore:
- Create strong and unique passwords for all of your accounts.
- If you have trouble remembering your passwords, a password manager has your back. It can help with generating passwords, too.
- Activate two-factor authentication, with one-time verification codes in text messages or an authenticator application, for every service that supports it. Otherwise, some anonymous raccoon that got its paws on your password will be able to read your secret correspondence or do something even nastier.
The 3 words are so easy to confused and people always get mixed up using them. Hope this article has made it clearer now!
Toxicity Online
I am one of those people who usually go online, most specifically, YouTube for content but very many a time, I go there just for the comments.
And over the years I have had a good laugh, but of late, the comment section fills me with dread. Take for example Tati Westbrook, A lifestyle guru who reviews beauty products. She reviewed a particular makeup palette and her view of things didn’t go down well with a section of the YouTube beauty community and the comment section became so vile she had to disable comments for that particular video.
Digital Security Tips for Women
An unfortunate number of women are becoming victims of cyber crimes. According to a recent study, more women are known to use the Internet to enrich their relationships compared to men. Young women, those 18-24, experience certain severe types of harassment at disproportionately high levels: 26% of these young women have been stalked online, and 25% were the target of online sexual harassment. The growing reach of the Internet and the rapid spread of information through mobile devices has presented new opportunities that could put some women at risk, so it’s important to be mindful of the dangers.